Engage in interactive sessions led by experienced mentors.
Gain exclusive access to Skolar's job portal for career opportunities.



To
No prior experience required; suitable for learners at all levels.



Learn through hands-on experience through projects



Engage in interactive sessions led by experienced mentors.

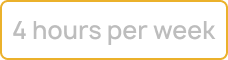
Join a comprehensive program spanning 12 weeks
Engage in interactive sessions led by experienced mentors.

No prior experience required; suitable for learners at all levels.

Learn through hands-on experience through projects
Gain exclusive access to Skolar's job portal for career opportunities.

Engage in interactive sessions led by experienced mentors.
Join a comprehensive program spanning 12 weeks

Full stack web development | Codedamn, Lifease Solutions
A seasoned developer with a flair for innovation, adept in NextJs, NodeJs, Astro Typescript, Prisma, tRPCs, and more. Known for delivering top-tier projects within deadlines and budget constraints, they thrive from personal endeavors to large-scale enterprise systems. With experience as a Software Developer at Lifease Solutions LLP and as a Fullstack Mentor at Skolar, they're dedicated to fostering excellence in budding developers while continually honing their own craft. Eager to embrace new challenges and opportunities, their passion for learning and growth propels them forward in the dynamic realm of web development.

Cyber security | Times of India, Indian Army
Ranjan Raja is a certified ethical hacker and an accomplished cybersecurity trainer with a Master of Technology from Punjab Technical University. With over 10 years of experience, he holds top-tier certifications including Certified Ethical Hacker (CEH) and Certified Secure Computer User (C/SCU) by EC-Council, Network Security Specialist by the International CyberSecurity Institute (ICSI), UK, and is skilled in AWS Identity and Access Management. Having conducted over 200 training sessions in ethical hacking, network security, and Linux architecture, Ranjan is dedicated to advancing cybersecurity knowledge and practices at Skolar’s e-learning platform.

Data structures and algorithms | EY, KMPG, Cognizant, Logic play
Shivendra K Jha is a seasoned software engineer with a robust background in backend development and a profound expertise in data structures and algorithms. Currently employed as a Software Engineer II at Zuora, he has honed his skills using Python Flask, Java, and databases such as Oracle and PLSQL. Shivendra’s professional journey includes significant tenures at EY, KPMG, Cognizant, and Logicplay, where he developed a strong foundation in problem-solving, object-oriented programming, and database management systems. Dedicated to producing high-quality work, Shivendra brings his commitment and expertise to Skolar, where he trains aspiring developers in mastering the complexities of data structures and algorithms.

Data science | EY and Neoastra
Sagar Rajput excels in applying neural and classical approaches to computer vision at Skolar, specializing in Convolutional Neural Networks (CNN) for object detection, face recognition, and image representation. He is adept in feature extraction, image augmentation, and designing custom CNN architectures using Pytorch. His expertise extends to technologies like InceptionNet, VGGNet, FaceNet, and SiameseNet. Sagar has also contributed to building an Image Data Lake, enhancing real-time analytics products. With professional stints at EY and Neoastra, he is a leading voice in data science education.

Curriculum designer | Zycus, BlackBuck Upgrad, Oracle
Anirban Paul is a seasoned Senior Data Scientist at Oracle with six years of rich experience spanning Data Science, Machine Learning, AI, and more. His past roles include impactful positions at companies like Wipro Digital, Anthem Inc, Zycus, and BlackBuck, where he developed AI-driven solutions for diverse industries. Anirban is passionate about using AI and data science to create innovative products, having built and maintained cutting-edge models and architectures. Skilled in a wide array of technologies from Python and TensorFlow to Azure and Google Cloud, he now shapes the future of tech education at Skolar as a Computer Science Curriculum Designer.

Machine Learning | IIT Madras
Praveen, an alumnus of IIT Madras, is a skilled Machine Learning Mentor at Skolar. With a strong focus on advanced AI techniques, Praveen guides students through the complexities of machine learning, combining theoretical knowledge with practical applications. His commitment to nurturing emerging talent in AI makes him an essential asset to Skolar's educational initiatives, helping students unlock their potential in the ever-evolving field of artificial intelligence.

Financial Analyst | Satya Securities, Motilal Oswal, Capital value Ventures
Ankita Bindal is a seasoned finance professional and mentor with over 16 years of combined experience in the industry and education. Specializing in professional courses, Ankita holds expertise in CFA, FRM, Financial Modeling, Private Company Valuation, and more, making her a sought-after corporate trainer and mentor for MBA finance students. She has crafted financial models for mergers and acquisitions, leveraged buyouts, and equity research, serving multinational corporations. Ankita's career includes roles as a Research Analyst at Capital Value Ventures, and as an Equity and Derivatives Advisor at Motilal Oswal and Fullerton Securities & Wealth Advisors Ltd.

Data structures and algorithms | Ericsson
Nishan Banga is a seasoned Solution Integrator and Software Engineer with extensive experience in developing robust customer service-oriented applications and innovative web technologies. Skilled in Java, JavaScript, Python, and C++, Nishan has a deep understanding of both web-based, multi-threaded applications and front-end development. He specializes in test automation strategies and has a solid grasp of Machine Learning and AI, including practical applications like cancer cell detection using Python.

Human Resource Management | Compitetoor, Erekrut, All About Lois
Astha Khurana is an accomplished HR professional, specializing in human resources and personality development. With a career spanning various roles, she currently also serves as a freelance Technical Recruiter and Tutor, enhancing her expertise in HR practices and soft skills training. Her diverse experience and educational background make her a valuable contributor to both corporate and academic environments in the field of Human Resource Management.
What do our students have to say about this course
4033 ratings
Leveled Up in Digital Domination!
I'm excited to announce my successful completion of an extensive Digital Marketing course.
In this rapidly shifting digital realm, I've armed myself for victory.
🔑 Unlocking my arsenal:
✅ SEO, SEM, SMM mastery
✅ Content wizardry for engagement
✅ Data alchemy for decisions
Big thanks to SKOLAR for this epic odyssey! 🙌 Ready to wield my skills for soaring success. 📈
Excited to announce the completion of my 3-month training and internship with Skolar in Full Stack Web Development! 🚀 Grateful for the hands-on experience and mentorship that has equipped me with the skills to tackle real-world challenges. Ready to embark on this next chapter in my journey as a full-stack developer! 💻
I am happy to share that i have completed my Internship in Cybersecurity from SKOLAR. Have gained knowledge in networking concepts, website hacking, windows hacking and security. Thank you Ranjan Raja our trainer for guiding us throughout the journey.
Delighted to share that I've successfully 💯completed the Machine Learning with Data Science course at SKOLAR ! 🎓 It's been an enriching journey diving deep into the world of data science, learning cutting-edge techniques, and acquiring practical skills that are invaluable in today's data-driven world. Grateful for the guidance of expert instructors and the opportunity to collaborate with fellow learners. Excited to apply my newfound knowledge to real-world projects and make a meaningful impact in the field of data science.💥
"I want to extend my gratitude to my instructor, Ranjan Raja, for his exceptional guidance throughout this intensive program. His industry expertise was invaluable in preparing me for a career in this field. The hands-on learning has equipped me with precisely the practical skills I need to excel as an ethical hacker. I look forward to applying everything I've absorbed and continuously expanding my capabilities. If you're interested in learning more about these topics or exploring a career in cyber security, I highly recommend checking out the SKOLAR program. Feel free to connect with me as well!
🚀Exciting News! Completed Machine Learning with Data Science Internship at SKOLAR 🚀
I am thrilled to share that I have successfully completed the Machine Learning with Data Science Internship program at SKOLAR. Throughout this immersive experience, I delved into the realms of Machine Learning.
🚀This achievement or internship not only represents my dedication to continuous learning but also demonstrates my commitment to staying at the forefront of data science and analytics. Thank you to my instructor Sagar Rajput 🔥
What do founders/recruiters have to say about this course
Having recently reviewed the MERN Stack course by Skolar, I'm impressed by its comprehensive coverage of MongoDB, Express.js, React.js, and Node.js. The practical approach, hands-on projects, and regular updates make it a valuable resource for aspiring developers. Highly recommended for those looking to enhance their skills in full-stack web development.
Ethical Hacker | Cyber Security Expert | Penetration Tester
Having recently reviewed the MERN Stack course by Skolar, I'm impressed by its comprehensive coverage of MongoDB, Express.js, React.js, and Node.js. The practical approach, hands-on projects, and regular updates make it a valuable resource for aspiring developers. Highly recommended for those looking to enhance their skills in full-stack web development.
Associate - Product Management at Bhive Workspace
Having recently reviewed the MERN Stack course by Skolar, I'm impressed by its comprehensive coverage of MongoDB, Express.js, React.js, and Node.js. The practical approach, hands-on projects, and regular updates make it a valuable resource for aspiring developers. Highly recommended for those looking to enhance their skills in full-stack web development.
Founder at Robostash pvt.ltd
Having recently reviewed the MERN Stack course by Skolar, I'm impressed by its comprehensive coverage of MongoDB, Express.js, React.js, and Node.js. The practical approach, hands-on projects, and regular updates make it a valuable resource for aspiring developers. Highly recommended for those looking to enhance their skills in full-stack web development.
Full Stack Developer
Having recently reviewed the MERN Stack course by Skolar, I'm impressed by its comprehensive coverage of MongoDB, Express.js, React.js, and Node.js. The practical approach, hands-on projects, and regular updates make it a valuable resource for aspiring developers. Highly recommended for those looking to enhance their skills in full-stack web development.
Data Structures and Algorithms
Our wide database of learners includes candidates that have settled into major companies like Amazon.
Fill the form and we’ll get back to you with all the details